Hacked my Uni's Alumni System web app
TL;DR : I discovered a broken access control vulnerability in UCY’s alumni system web app that allowed me to change other users’ passwords.
Observation
- In June 2024 I graduated (🎉) from the Computer Science Department at the University of Cyprus, and joined the UCY’s alumni system web app.
- During account registration, I wasn’t able to choose my own password; instead, a cleartext password was sent to me via email (🤔).
- This made me curious about the overall security of the app, and I wondered if I could uncover any critical vulnerabilities.
Identifying the vulnerability
- I noticed that the app has a reset password functionality.
- For this feature, a
POSTrequest was being sent to the/pub_alumni_open/ALUMNI_V2.alumnis_pck.exec_resetendpoint with two arguments:emailandnew_password. - I tested the password reset process by attempting to reset my own password while modifying the session cookie to check if it was properly validated.
- To my surprise, the password was successfully updated even with an invalid session cookie.
- Next, I removed the session cookie entirely and sent the password reset request again.
- Once again, the password was successfully updated. At this point I confirmed that the application did not verify whether the user requesting the password change is the actual owner of the email for which the change request is made (Broken Access Control).
- In fact the session cookie was not checked at all, meaning a completely unauthenticated
POSTrequest to the password change endpoint could succeed.
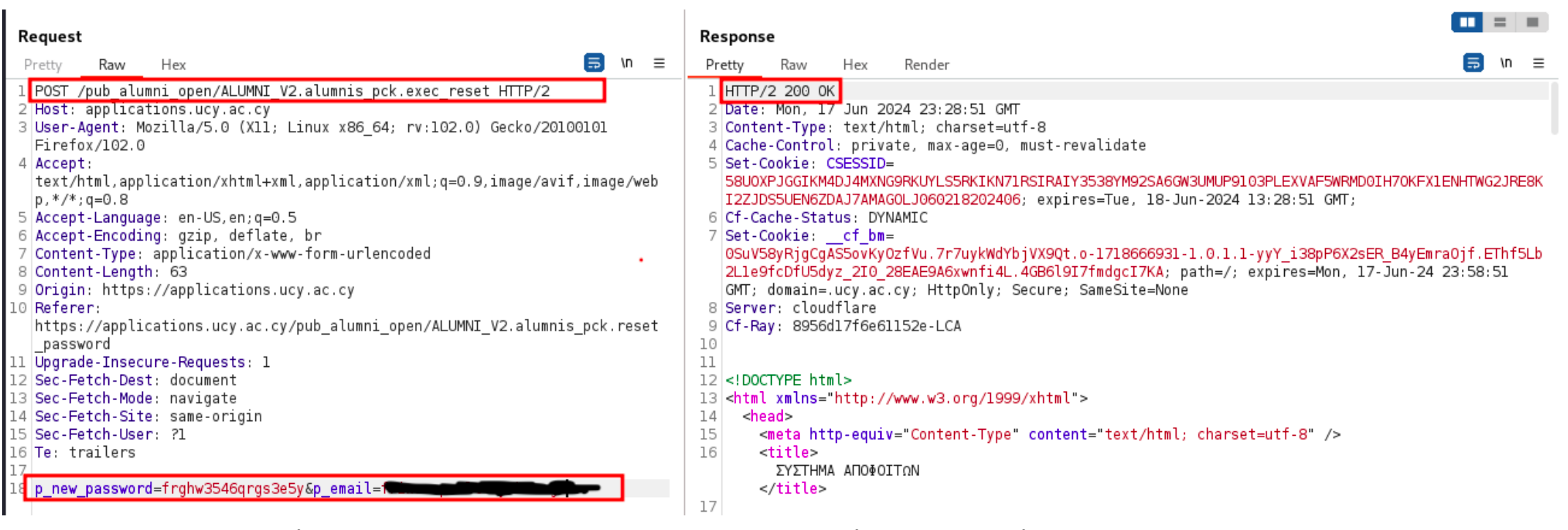
Notice the absence of the session cookie and the successful response.
Exploiting the vulnerability
Extra testing accounts
- I wanted to test whether I could create additional accounts, and attempt to change their passwords using unauthenticated requests.
- Although this app is intended exclusively for UCY alumni, I was able to create a second account using the same ID and even a fake ID like
111111 - This indicates that an attacker could likely create an account without being a UCY graduate.
Testing
- From
accountAI tried to changeaccountB’s password. - First, I intercepted the password reset request from
accountA, modified the email parameter toaccountB, and forwarded the request. - Then, I logged into
accountBusing the newly updated password to confirm the change. - Everything worked as expected, proving that the vulnerability is exploitable.
Reporting
- I reported this bug to UCY’s IT infrastructure team, emphasizing its HIGH risk level.
- In my report, I included detailed steps to reproduce the issue and provided the following recommendations:
- The application must deny any unauthenticated requests or redirect them to the login page.
- During a password change request, the application should verify that the email belongs to the user associated with the session cookie included in the request.
UCY’s response
- The Acting Head of UCY’s “IT Infrastructure Service” sent me an email to thank me and informed me that my report was being forwarded to UCY’s “Information Applications Services” and other security professionals.
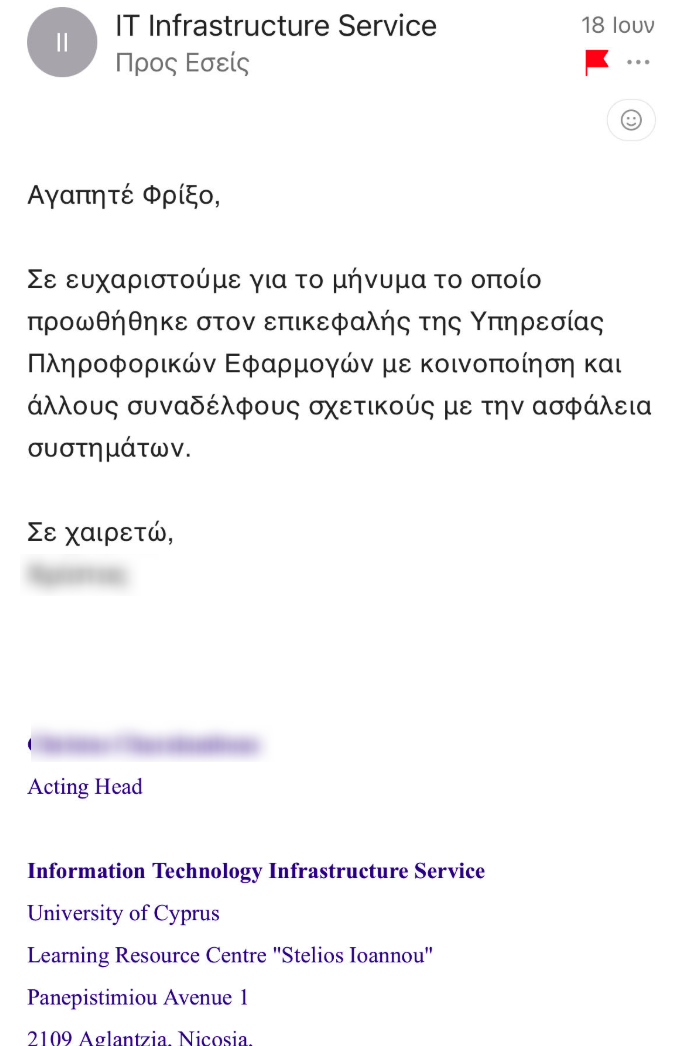
- The next day, I received a phone call from the “Information Applications Services” team to thank me once again.
- Two weeks later, the app was updated, and the issue was resolved.
Enjoy Reading This Article?
Here are some more articles you might like to read next: