Race Condition Bug in the Most Popular Greek E-Commerce App
TL;DR : I found a race-condition bug in a popular greek e-commerce app, that allowed me to redeem the same gift-card twice.
Race conditions
- Back in October 2023, I was hunting bugs in a popular greek e-commerce app. Around that time, PortSwigger’s Web Security Academy published new content on race condition vulnerabilities. This prompted me to explore the app for such issues.
- Race conditions usually occurr when websites handle requests in parallel without adequate safeguards, leading to “collisions” that result in unintended behavior.
- This type of vulnerability is similar to business logic flaws.
- In a race condition attack, an attacker sends carefully timed requests to intentionally create collisions and exploit the resulting unintended behavior for malicious purposes.
Limit overrun race conditions
- The most common type of race condition allows an attacker to bypass some kind of limit imposed by the application’s business logic.
- For instance, consider an e-shop where a customer wants to use a one-time discount code. The application might handle the process as follows:
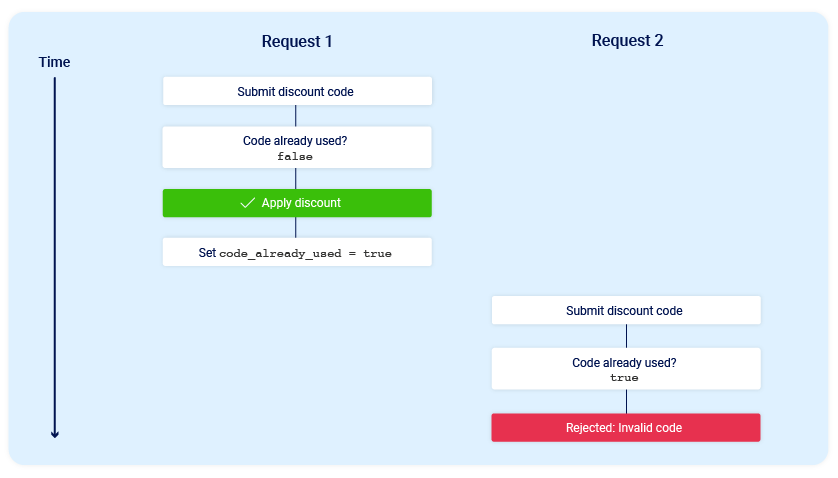
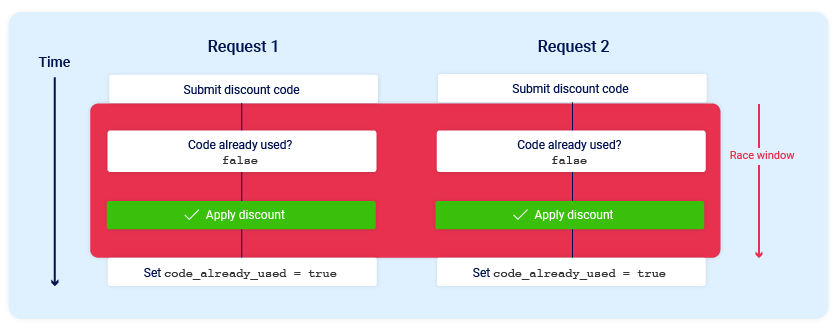
- Now consider what would happen if a user who has never applied this discount code before tried to apply it twice at almost exactly the same time:
Images from Portswigger's web-security Academy
- The application enters a temporary sub-state during its operation.
- This sub-state starts when the server begins processing the initial request and ends once the database is updated to reflect that the discount code has been used.
- During this brief window, a race condition occurs, allowing users to repeatedly claim the discount multiple times.
- There are many variations of this kind of attack, including:
- Redeeming a gift card multiple times (😉)
- Rating a product multiple times
- Withdrawing or transferring cash in excess of your account balance
- Reusing a single CAPTCHA solution
- Bypassing an anti-brute-force rate limit
Testing for race condition vulnerabilities
Understanding the gift card functionality
- The app allows users to purchase gift cards, so I bought one to test for any potential limit overruns.
- I noticed that the gift card was not linked to any specific account, likely to allow it to be gifted to anyone.
- I created three different accounts and confirmed that all of them could apply the gift card code during checkout, though not simultaneously.
Discovering race conditions
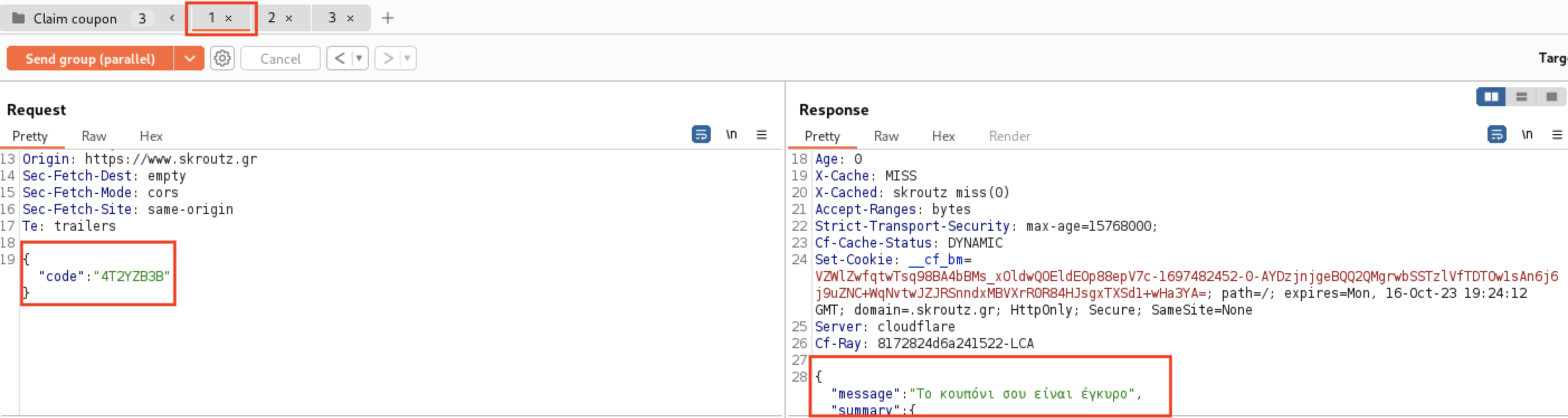
- During checkout, when a user added a coupon, a
POSTrequest whas being sent to the/coupons/claim.jsonendpoint, containing the code in a JSON, such as{"code":"XXXXXXX"}. - I sent this request to Burp Repeater, for each session from all three accounts (I used three different browsers to create separate sessions, one for each account - although this could also be done in the same browser using a browser extension).
- Burp Repeater allows you to create a tab group and add multiple requests together.
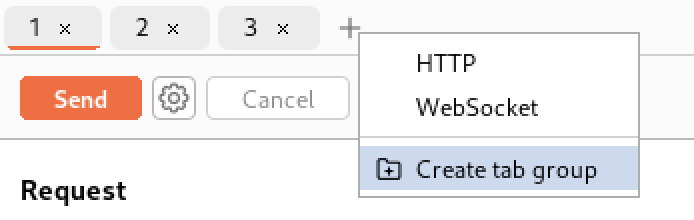
- Once I added all three requests to the group tab, I sent them in parallel.
- Sending requests in parallel requires Burp Suite 2023.9 or later!
- By observing the responses, I discovered that the coupon was applied to more than one account!
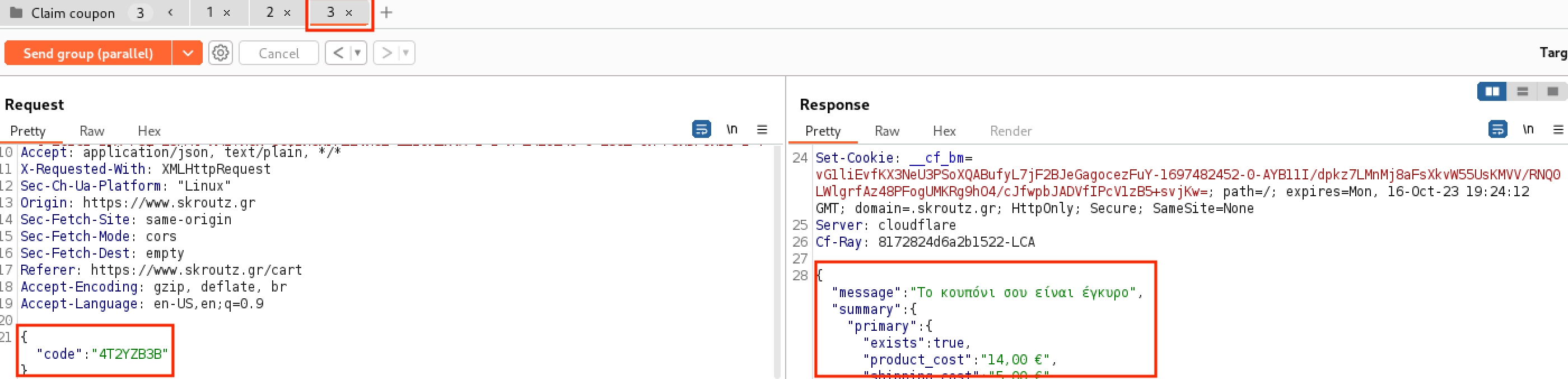
- While I couldn’t get the coupon to apply to all three accounts simultaneously, 90% of the time, it was successfully applied to two of the three.
- I did not attempt to complete a purchase, but I verified that you can proceed through the entire checkout process up to the payment step. Therefore, this vulnerability is exploitable.
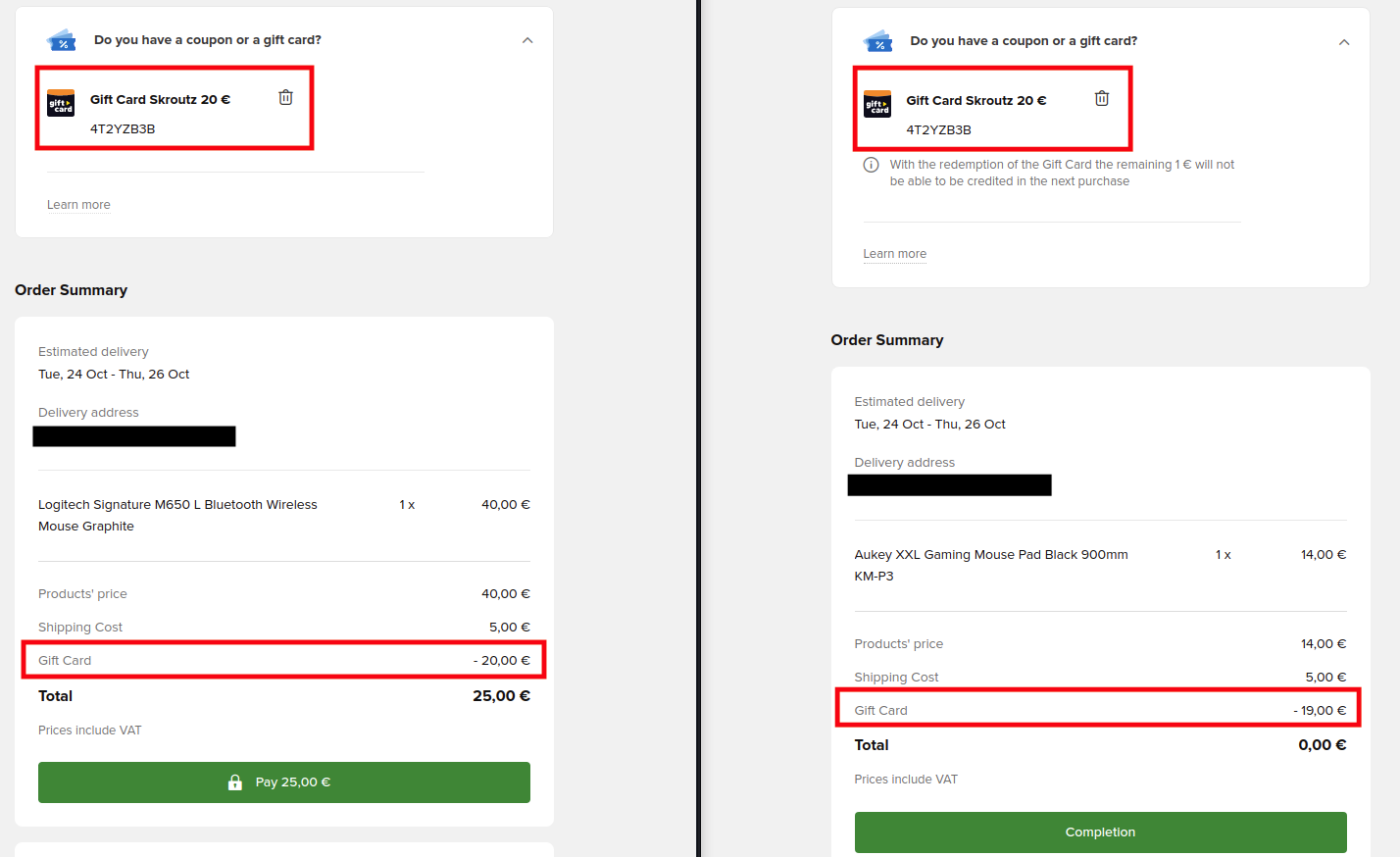
- The maximum amount for a gift card that can be purchased is €150, so an attacker could pay €150 and use it to buy €300 worth of items—repeating this process an unlimited number of times.
Reporting
- This app has a bug bounty program in BugCrowd, so I reported the issue there.
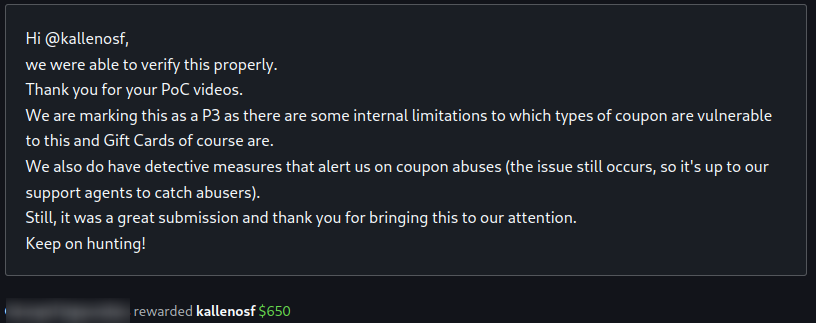
- At first, they couldn’t reproduce the issue and requested some PoC videos, which I provided.
- The bug was classified as a
P3and I was awarded$650.
- This was my second finding in the same app, as I had previously discovered a business logic vulnerability that was classified as
P4.
Enjoy Reading This Article?
Here are some more articles you might like to read next: